Covert Channel DLP
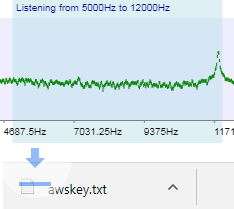
Protection for the latest data leakage vulnerabilities.Determined insiders have found new ways around Traditional DLP to take data undetected. Stop them from taking your data.
Security Analytics
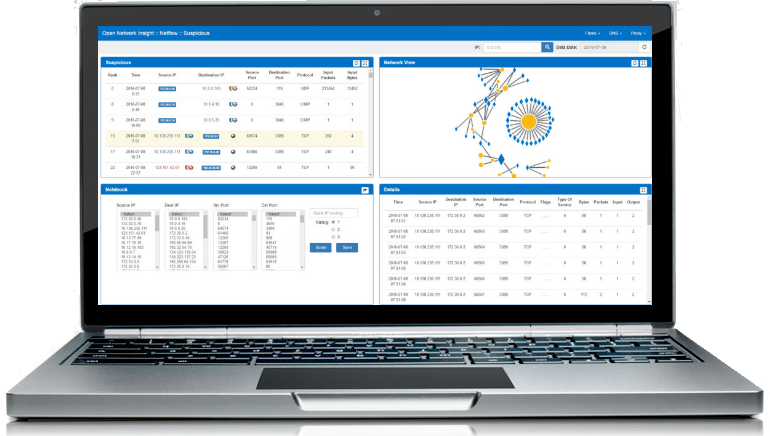
Identify sophisticated internal and external threats.Model activity in your organisations systems and network to identify unusual behaviour. Powerful machine learning detects APTs, fraud and insider collusion can be detected.
Security Design & Integration
Our experts can design security into your environment. We review businesses operations, identify vulnerabilities and come up with the best way to add protection, minimising cost and intrusiveness.Difficult to solve IT security problems are met with innovative and practical solutions. We help design your procedures and environment to protect your systems & data assets. We are on hand to help integrate our security products, deploying and configuring systems and infrastructure.
Vulnerability Focussed
Our protections are specifically targeted at data leak vulnerabilities that other platforms don't cover.
Cutting Edge Leak Protection
We work with security researchers & hackers to secure against the latest ex-filtration techniques.
Easy Integration
Fast install & roll-out for instant protection. Smooth integration with your existing SIEM / security logging tools like Splunk.
Policy Control
Comes with pre-configured but customisable Options to control detection, notification, escalation and taking protective action.
Identify Rogue Insiders
By correlating many data points we can focus investigation onto insiders behaving unusually.
Sophisticated Threat Detection
Identify complex threats through machine learning analysis across data sources to highlight unusual activity.
Specialist Expertise
We can guide you on integrating our systems and on cyber-security in general. We provide proactive upgrade assistance when new features are available.
Dedicated support
Our team is on-hand to help you deploy, run and support our DLP & Security Analytics. Minimal resources are needed for maintenance.