Loading...
Data Leakage Resources
EXPLOITS & VULNERABILITY RESEARCH
Research into how to break data out of secure systems can inspire data leak protection systems to prevent the vulnerabilities revealed from being exploited DLP with a "black-hat" mentality: finding ways to break data out to find the holes. Most of these exploits rely on malware initially compromising the target machine, unlike the Data Border proof of concept ex-filtration tools which are based on a rogue insider with only normal non-elevated access wishing to bypass DLP; they do however illustrate the kinds of techniques and channels used to ex-filtrate the data.
 Inaudible Sound as a Covert Channel in Mobile Devices
Inaudible Sound as a Covert Channel in Mobile Devices
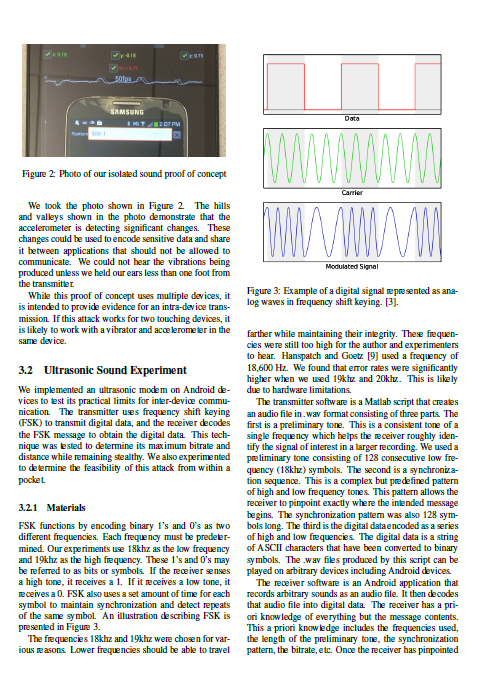
Explores the unconventional methods attackers will begin to use for ex-filtrating data as devices become more secure, focussing on vibrations and sound to send signals up to 100 feet away.
Cached from here
 DiskFiltration Data Exfiltration from Speakerless Air-Gapped Computers via Covert Hard Drive Noise
DiskFiltration Data Exfiltration from Speakerless Air-Gapped Computers via Covert Hard Drive Noise
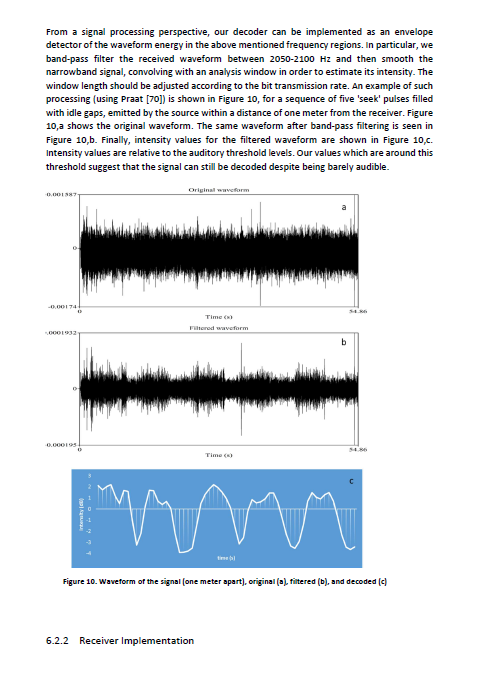
A covert channel to leak of data from a computer by manipulating the movements of the hard drive's actuator to emit sounds without the presence of speakers or audio hardware.
Cached from here
 Covert Channels Using Mobile Devices Magnetic Field Sensors
Covert Channels Using Mobile Devices Magnetic Field Sensors
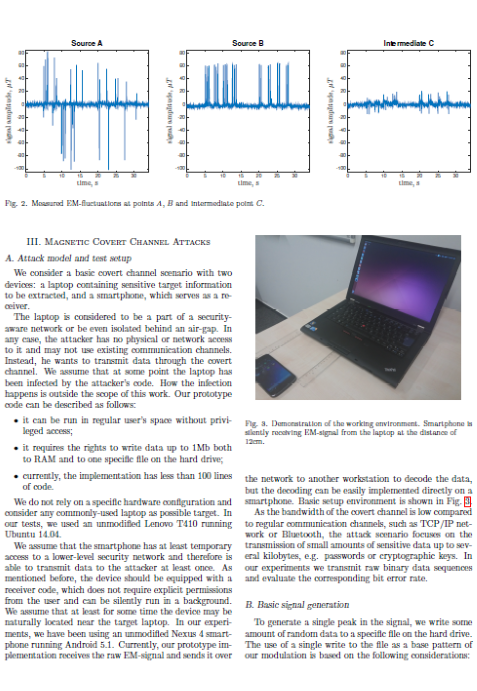
Develops a covert channel using magnetic field changes induced by computer components in IO operations (movement of the hard drive magnetic head) and picked up by smartphone magnetic sensors.
Cached from here
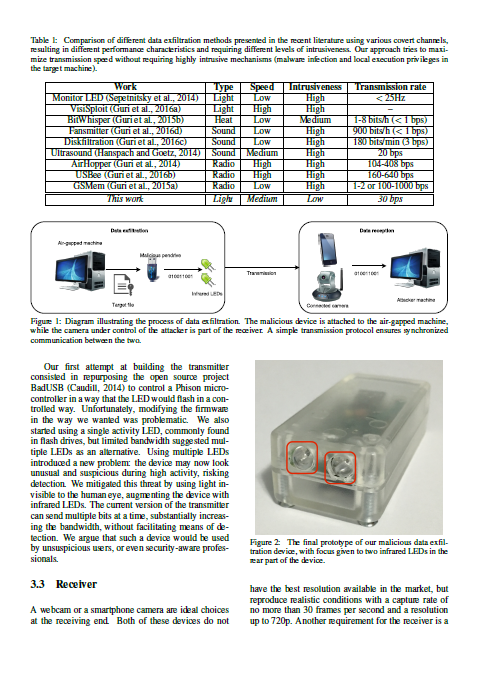
 Platform-agnostic Low-intrusion Optical Data Exfiltration
Platform-agnostic Low-intrusion Optical Data Exfiltration
Involves a modified USB storage device which ex-filtrated data covertly by blinking infra-red LEDs.
Cached from here

 Air-gap Limitations and Bypass Techniques - electromagnetic
Air-gap Limitations and Bypass Techniques - electromagnetic
Data transfer over an air-gap by intentionally creating electromagnetic interference for use as a covert data channel and an FM receiving smart-phone as the untrusted system to which the data is ex-filtrated.
Cached from here

 Fansmitter Acoustic Data Exfiltration
Fansmitter Acoustic Data Exfiltration
Use of a system fan to produce a signal from vibrations over which data can be transferred, even in systems which are air-gapped and the speakers have been removed to create an 'audio-gap'.
Cached from here

 VisiSploit An Optical Covert-Channel to Leak Data through an Air-Gap
VisiSploit An Optical Covert-Channel to Leak Data through an Air-Gap
An Optical Covert-Channel to Leak Data through an Air-Gap via an LCD computer monitor using QR codes shown with low contrast or within fast flickering images to avoid detection with the human eye but still recover data by recording the screen with a camera.
Cached from here

 xLED Covert Data Exfiltration from Air-Gapped Networks via Router LEDs
xLED Covert Data Exfiltration from Air-Gapped Networks via Router LEDs
An approach to covertly leak data (e.g., encryption keys, passwords and files) from highly secure or air-gapped networks via status LEDs in networking equipment like routers.
Cached from here

 IREXF Data Ex-filtration from Air-gapped Networks by Infrared Remote Control Signals
IREXF Data Ex-filtration from Air-gapped Networks by Infrared Remote Control Signals
A novel infrared optical covert channel from a well-protected air-gapped network via a malicious infrared module implanted into a keyboard.
Cached from here

 Ex-filtration of Data from Air-gapped Networks via Unmodulated LED Status Indicators
Ex-filtration of Data from Air-gapped Networks via Unmodulated LED Status Indicators
Data ex-filtration using system LEDs with binary frequency shift keying(B-FSK) replacing on-off keying(OOK) to improve the imperceptibility as covert communication.
Cached from here

 AirHopper Bridging the Air-Gap between Isolated Networks and Mobile Phones using Radio Frequencies
AirHopper Bridging the Air-Gap between Isolated Networks and Mobile Phones using Radio Frequencies
AirHopper bridges the air-gap between an isolated network and nearby infected mobile phones using FM signals emitted from the graphics card.
Cached from here

 Air-Gap covert channels Carrara_Brent_2016_thesis
Air-Gap covert channels Carrara_Brent_2016_thesis
Extensive discussion of out-of-band covert data leak channels (acoustic, light, seismic, magnetic, thermal, and radio-frequency), techniques, covertness and transfer rates.
Cached from here

 On Covert Acoustical Mesh Networks in Air
On Covert Acoustical Mesh Networks in Air
Uses audio modulation/demodulation to exchange data between systems through air (originally designed for underwater) to circumvent system and network policies by establishing communications that have not been considered in the design of the computing system.
Cached from here

 Bridging the Air Gap Inaudible Data Ex-filtration by Insiders
Bridging the Air Gap Inaudible Data Ex-filtration by Insiders
Presents a method that insiders can use to facilitate data ex-filtration from air-gapped systems without using any modified hardware using inaudible sounds transmitted from the target machine’s speakers to transfer data to a nearby computer equipped with a microphone.
Cached from here

 GSMem Data Exfiltration from Air-Gapped Computers over GSM Frequencies
GSMem Data Exfiltration from Air-Gapped Computers over GSM Frequencies
Malware that ex-filtrates data through an air-gap over cellular frequencies. Rogue software on an infected target computer modulates and transmits electromagnetic signals at cellular frequencies by invoking specific memory-related instructions and utilizing the multichannel memory architecture.
Cached from here

 Data Ex-filtration and Covert Channels
Data Ex-filtration and Covert Channels
A discussion of data ex-filtration methods, their bandwidth, covertness and maliciousness.
Cached from here
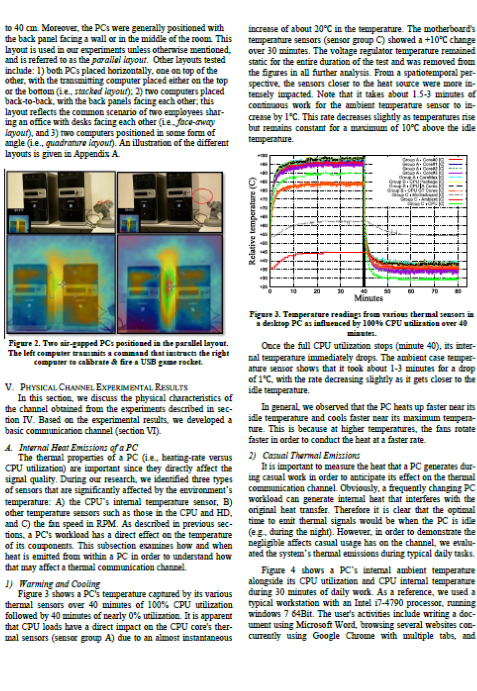
 BitWhisper Covert Signalling Channel between Air-Gapped Computers using Thermal Manipulations
BitWhisper Covert Signalling Channel between Air-Gapped Computers using Thermal Manipulations
A method of bridging the air-gap between adjacent compromised computers by using their heat emissions and built-in thermal sensors to create a covert bidirectional communication channel with no additional hardware.
Cached from here

 Through Glass XFER Screen Data Transfer
Through Glass XFER Screen Data Transfer
A suite of tools that demonstrate the unauthorised infiltration and ex-filtration of code and data through secure networks; A way to download files through a screen (even via an ANSI terminal window) and a way to upload files through the keyboard interface.
Cached from here

 Leaking Data from Air-Gapped Computers via the Hard Drive LED
Leaking Data from Air-Gapped Computers via the Hard Drive LED
Blinks the hard disk drive (HDD) activity LED which exists in most of today’s desktop PCs, laptops and servers to ex-filtrate data
Cached from here
DATA LOSS COST, RISK AND IMPACT SURVEYS
Assessments of the size, scale and impact of data loss on organisations.

 Ponemon 2017 Cost Cyber Crime
Ponemon 2017 Cost Cyber Crime
Analyses the costs and impacts of cyber crime on businesses as the number of successful breaches per company each year rises: information loss represents the largest cost component.
Cached from here

 Ponemon 2017 Cost Of Data Breach Study
Ponemon 2017 Cost Of Data Breach Study
Examines the costs and impacts of data breaches on businesses: the average total cost is decreasing but breaches are getting larger. Analysis breaks down by root cause, industry & country and shows factors influencing the cost.
Cached from here

 Ponemon 2016 The Cybersecurity Risk to Knowledge Assets
Ponemon 2016 The Cybersecurity Risk to Knowledge Assets
Conducted to determine whether the publicity accorded data breaches subject to notification laws and related regulatory requirements has skewed the focus of organizations away from the theft or loss of their most critical information
Cached from here

 Ponemon 2016 Data Theft Press Release
Ponemon 2016 Data Theft Press Release
Highlights the key risks of data theft to organisations and asserts that they are unprepared to protect what matters most to them
Cached from here

 HP Cyber Security And Your Business
HP Cyber Security And Your Business
Examines common Cyber security myths, the impact of cyber crime on businesses and the future of business cyber security.
Cached from here
DLP MARKET COVERAGE REVIEW
Like most technology sectors nowadays, there is good market coverage by the review panels of Forrester and Gartner. They give interesting insight into the state of the market, trends and what the factors are to judge DLP solutions by as well as reviewing the offerings of the large enterprise providers.
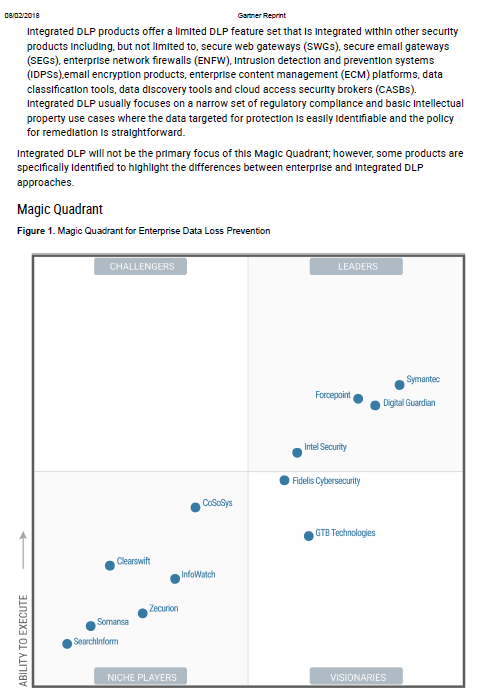
 Gartner Magic Quadrant for Enterprise Data Loss Prevention 2017
Gartner Magic Quadrant for Enterprise Data Loss Prevention 2017
Security and risk management leaders purchase on-premises enterprise DLP to solve for either organization wide regulatory compliance or to better protect specific types of intellectual property, while monitoring emerging cloud DLP capabilities. Gartner defines the DLP market as those technologies that, as a core function, provide remediation for data loss based on both content inspection and contextual analysis of data.
Cached from here

 The Forrester Wave Data Loss Prevention Suites Q4 2016
The Forrester Wave Data Loss Prevention Suites Q4 2016
Evaluates and scores the 7 most significant data loss prevention suite providers. Symantec, Digital Guardian, and Forcepoint lead the pack. IP Protection, Info Management, And Endpoint Visibility And Control Are Key Differentiators
Cached from here
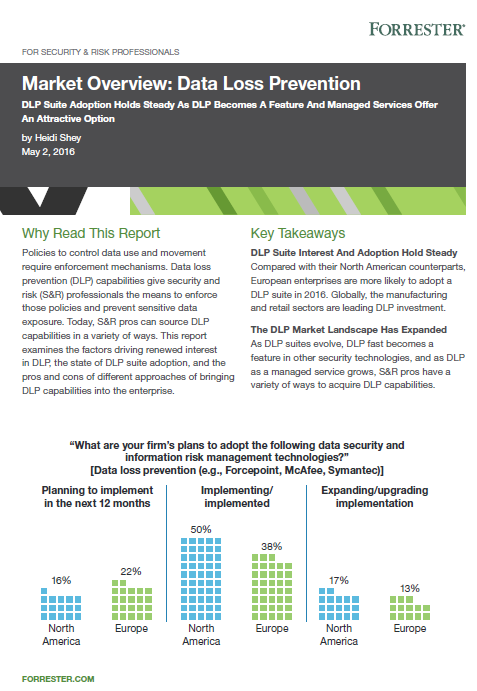
 Forrester Market Overview Data Loss Prevention
Forrester Market Overview Data Loss Prevention
Examines the factors driving renewed interest in DLP, the state of DLP suite adoption, and the pros and cons of different approaches of bringing DLP capabilities into the enterprise.
Cached from here

 Forrester Vendor Landscape Data Loss Prevention Solutions
Forrester Vendor Landscape Data Loss Prevention Solutions
Highlights the different channels of data loss and examines the varied landscape of vendors offering DLP capabilities today as a feature, standalone solution, or suite
Cached from here

 DLP Experts Data Loss Prevention Leading Vendor Review Q4 2016
DLP Experts Data Loss Prevention Leading Vendor Review Q4 2016
Focuses on Data Loss Prevention technologies and the DLP marketplace at large. Provide an overview of select Data Loss Prevention (DLP) vendor technologies.
Cached from here