Data Ex-Filtration Screen-shots
This example shows just how easily sound and screen based data transfer can be used to extract data from
an organisations controlled network. This is a working Proof Of Concept of the vulnerabilities using just
web pages to perform the sending and receiving of data, running in a normal browser with no unusual, admin or elevated permissions
– to Traditional DLP & the security team it looks just like any other web page.
Data Transfer / POC Ex-filtration Tools
1: Send Text As Sound From Corporate Machine
Simple text data can be broadcast from the sound sending page to a receiving over the computers audio speaker / headphones / aux jack. This helps to quickly gauge what frequencies can be sent / received with the current hardware with the current levels of ambient background noise.
Several pre-sets are provided with varying speed, human audible / inaudible frequencies, susceptibility to background noise and requiring the speaker and microphone to output / receive those frequencies.
2: Send File As Sound From Corporate Machine
When a reliable / desired set of frequencies has been chosen according to speed, the environmental noise, audio hardware capabilities and if ultra-sonic non-detectability is desired, a larger file based payload can be sent.
Simply select the file and it will be output
3: Receive Sound On External Machine
On a different computer which is connected to a different network, the sound receiver webpage is loaded and set to listen to the same frequency range as the sender is broadcasting on. The same pre-sets are available to quickly set the frequency.
As a sound encoded message is received, the frequency peaks can be seen on the graphic equalizer and are decoded to the message. Text based messaged are shown in the “received message history”.
As a message is being received containing an encoded file, a status message is shown above the graphic equalizer showing the filename and percentage received so far.
When the file message has been fully received the file contents are decoded and saved as a normal browser download (to the downloads folder) but without the file having passed over any network.
1: Send Text Via On Screen QR From Corporate Machine
The QR sending vulnerability POC also has the capability to send a text message encoded as a QR code, which is updated as the message is typed.
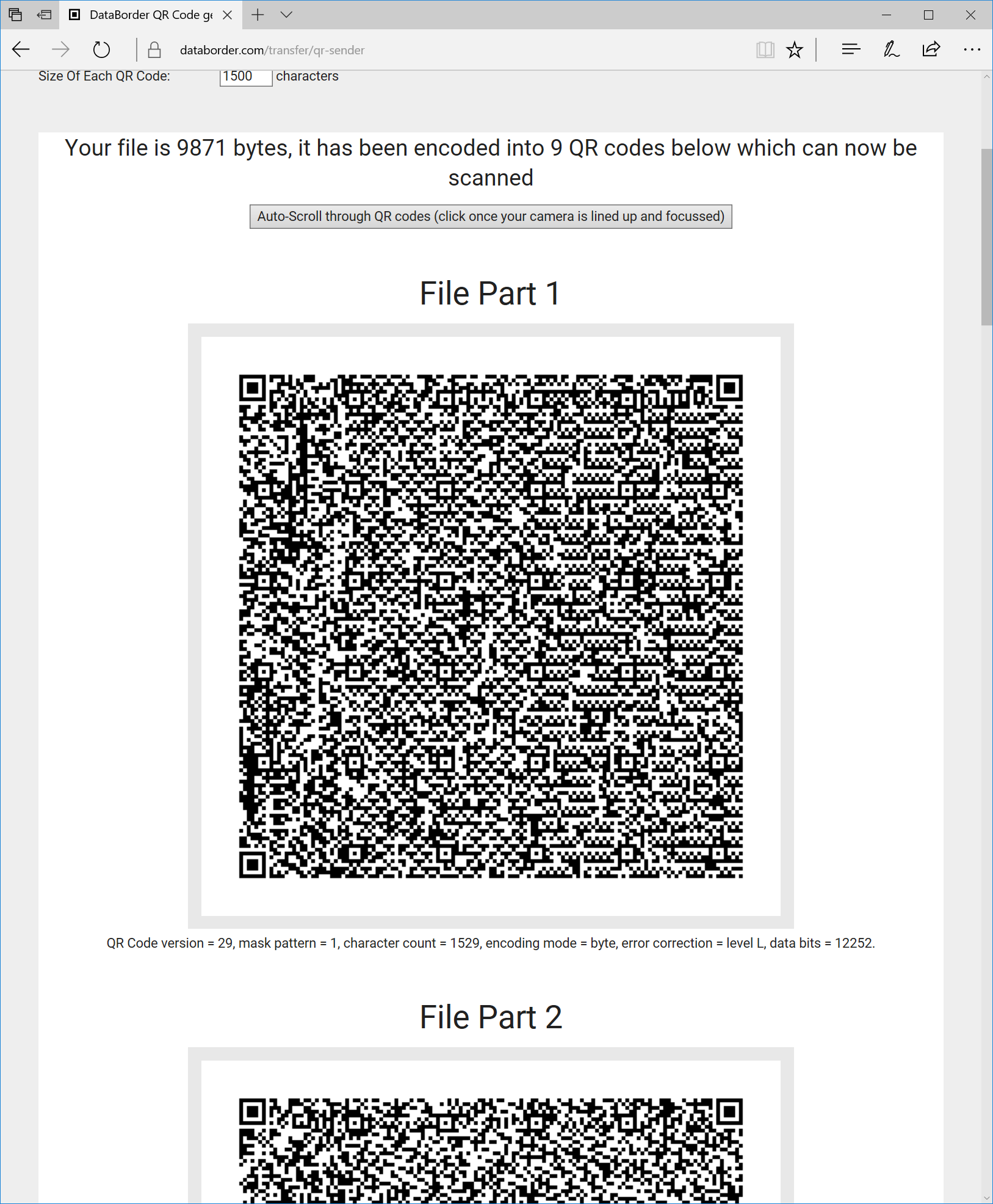
2: Send File Via On Screen QR From Corporate Machine
A file can also be encoded into a series of QR codes by simply selecting the file to be read in by the browser. The QR code is generated dynamically within the webpage so the file it not transferred over the network.
Simply select the file and it will be encoded (in javascript) in the browser.
The output of the file encoding is displayed as a sequence of QR codes which can then be scrolled through as they are scanned into the receiver. A file of 500Kb takes around 400 QR codes, but an automatic scroll is provided to sequence through them in the same region of the screen to allow straightforward capture of the QR codes by the receiver.
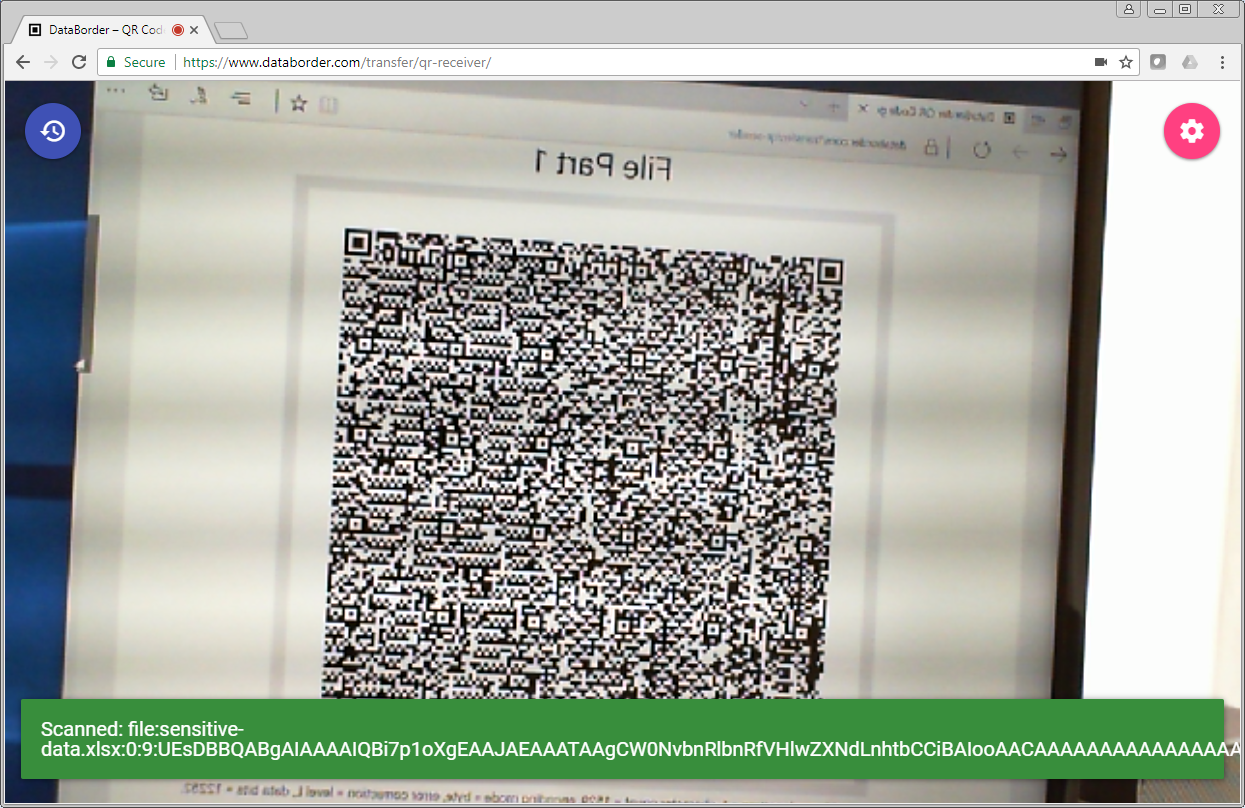
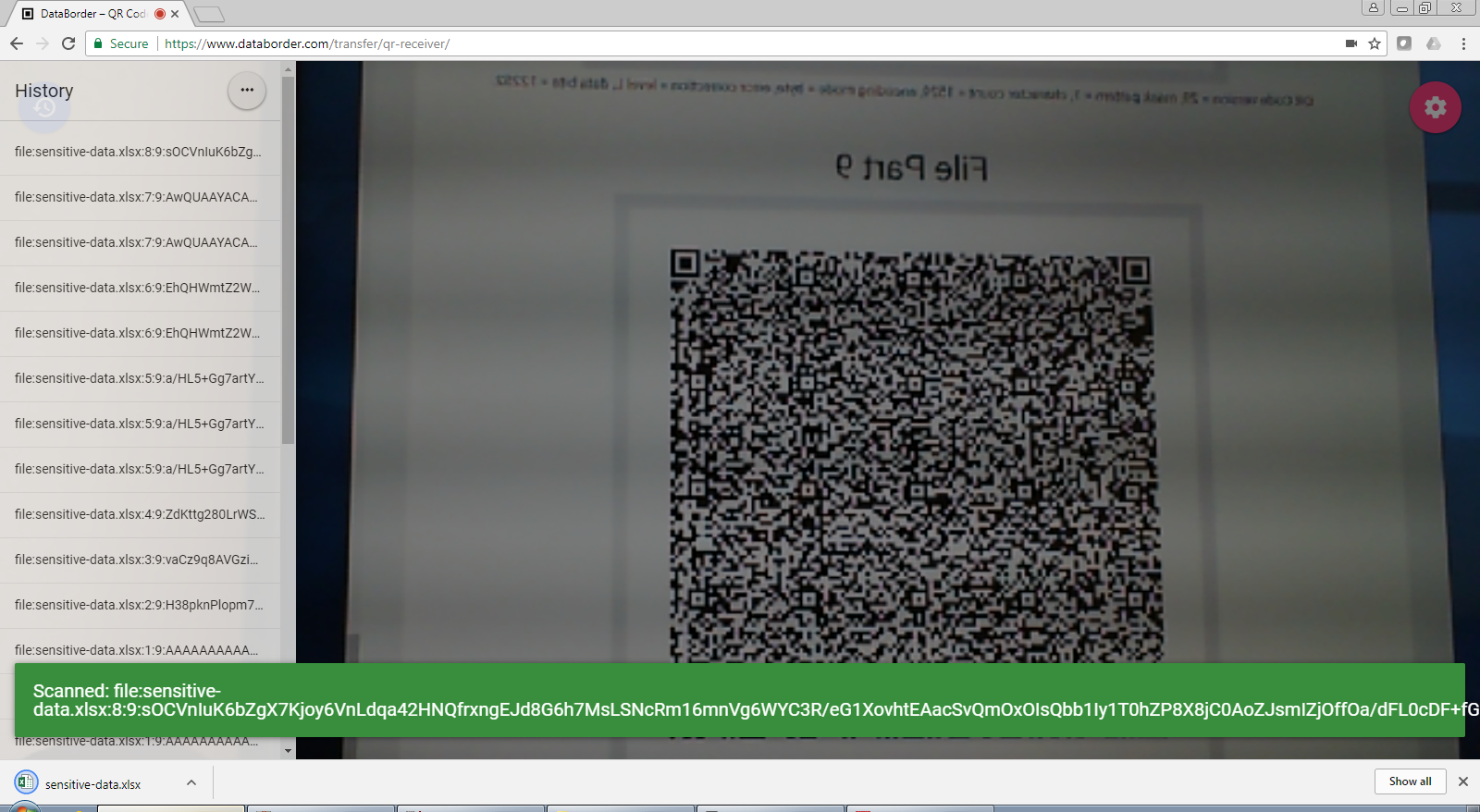
3: Read QR Code On External Machine
On a different computer which is connected to a different network, the screen receiver webpage is loaded.
As multiple codes are scanned they are retained until all of the file parts have been received. This has the effect of a data-blast which is digitally recorded in the receiving browser.
When all of the parts of a file have been received, the message can be reassembled and decoded then saved as a normal browser download into the downloads folder on the receiving computer but without the file having been transferred over the network.