Build: Threat Defence
Technical and Process Expertise
Threat Defence implements technical and organizational capabilities carefully aligned to business needs and financial context.
Threat defence first secures applications and infrastructure, reviews and grants appropriate user access, enables situational awareness
 across technical assets, forms technical and cross functional business response plans and finally validates capabilities through simulated attacks.
across technical assets, forms technical and cross functional business response plans and finally validates capabilities through simulated attacks.
Our experience has shown that many clients have technology tools already in place that are not effectively configured or are misaligned with how the business functions. We have also found business process and cross-team junctions that can function more effectively, such as with an external managed security service provider (MSSP) or between security engineering and operations. Data Border can ensure organizations receive the full value of these investments.
Conventional definitions of application security apply less as organizations rely more on hybrid architectures with cloud services and software as a service. Instead, we map where sensitive data flows in motion, where it used, and where it is stored.
Methodology: Threat Defence Implementation
- In motion: firewall, IDS/IPS, data loss prevention, email defences, trading partner APIs
- At use: application coding practices, encryption/obfuscation
- At rest: database and storage configuration, physical security
- Including impersonation and application accounts
- Provide a neutral third party to diplomatically challenge access needs
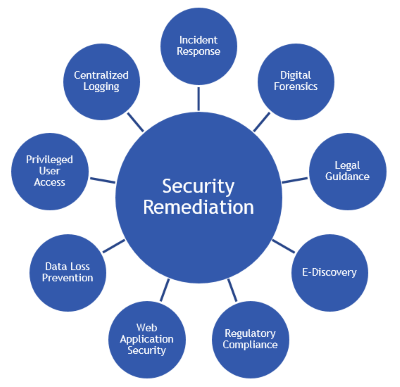
- Centralized logging and analytics
- SIEM configuration
- Data loss prevention
- Standard operating procedures to respond and contain an incident
- Technical run book with specific hands-on actions
- Cross functional actions focused on preserving customer relationships
- Prepare for investigation, litigation, or insurance claims
- Prepare the team
- Test and improve response plans
- Validate capabilities
- Our team is always on hand and regularly in touch
- Review and adjust defences as circumstances change
- Aware of and alert to new vulnerabilities
Implementing Cybersecurity defences typically follows on from our Security assessment and planning, but we can help with implementing specific defences if needed. Please also see our SOC/CIRT Effectiveness service for in-depth capabilities development.
Please contact us for a free initial discussion covering the defences you already have and what you'd like to put in place.