Loading...
Cybersecurity Consulting
Operate Confidently
Security incidents will occur. Data Border brings leaders confidence that their organization is well-prepared. The Data Border methodology applies a results-focused approach implementing the NIST Cybersecurity Framework. We apply insights, tools, and hands-on expertise developed protecting sophisticated, global companies. We streamline the methodology to core essentials for medium-sized organizations.
Plan: Security Assessment
Read more..
Build: Threat Defence
Read more..
Operate: SOC/CIRT Effectiveness
Read more..
Counter: Incident Response
Read more..
The Process
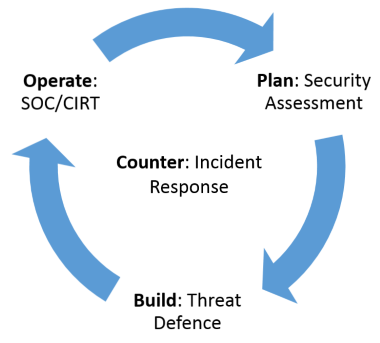
We help organizations get started on the continuous cycle of improving and adapting their defences to address the risks appropriate to their business and the environment they operate in.