Loading...
Covert Channel Data Loss Prevention
Not all insiders are trustworthy
Information can make the difference between success and failure. Competitors getting your trade
secrets gives them the advantage you have worked or invested to build.
Employees know the ideas & plans, sensitive data, designs & computer code. A disgruntled or outside influenced employee can work against the organisation, stealing & divulging information they have been trusted with. Pressurised work environments heighten the risk, as do redundancies, restructuring and economic pressure.
Insiders know what to take and how to use it.
Employees know the ideas & plans, sensitive data, designs & computer code. A disgruntled or outside influenced employee can work against the organisation, stealing & divulging information they have been trusted with. Pressurised work environments heighten the risk, as do redundancies, restructuring and economic pressure.
Insiders know what to take and how to use it.
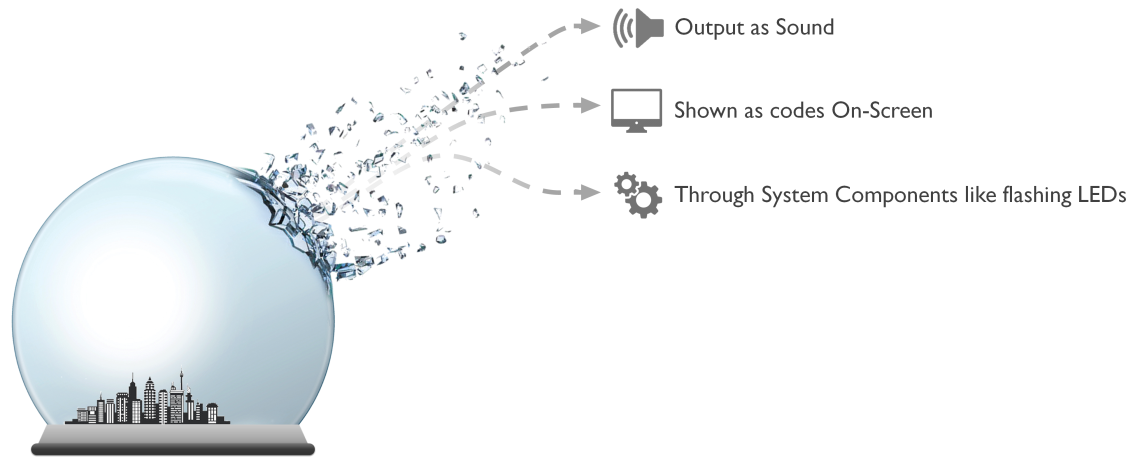
Theft methods have evolved protection
... But
Regular data transfer methods are now well secured at the perimeter.
Systems even have some success predicting and detecting rogue insiders.
Systems even have some success predicting and detecting rogue insiders.
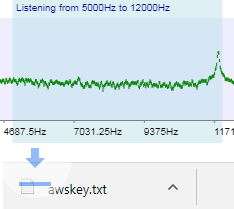
Determined Insiders have found ways to extract data through unorthodox, covert means.