PLAN: Security Assessment
Rigorous Assessment, Practical Solutions
Data Border's Security Assessors can undertake a detailed study of your IT security and identify improvements to secure the systems. An assessment for security is potentially the most useful of all security tests. It will reduce your IT risk and manage policy compliance with internal security policies and external regulations. The Security Review provides an authoritative assessment with a practical plan to rapidly safeguard operations.
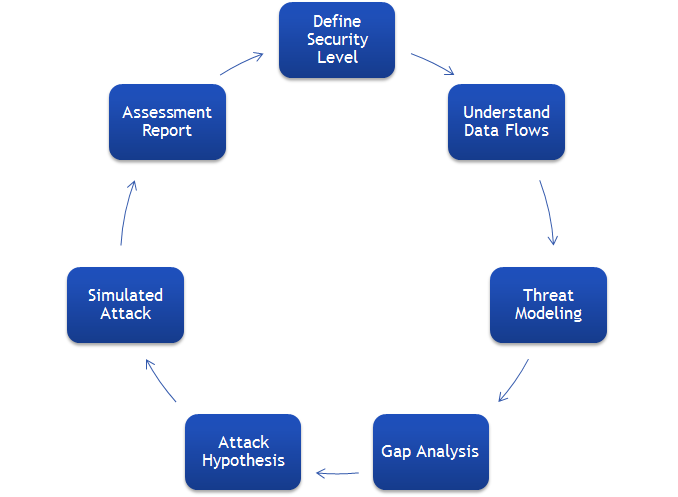
We work with clients at the start of the assessment to target the scope, focussing on the areas which present most risk to their business. By taking this approach we calibrate our efforts to help our clients guard against threats using the appropriate level of security for them. Our approach identifies actions needed to resolve any security weaknesses to achieve targeted security levels based on business needs.
Areas Covered
- Define appropriate security levels balancing impact, probability, and costs
- Determine regulatory mandates and contractual obligations
- Technical: physically confirm user privileges; application, database, network, and server configuration; and existing security technology such as firewalls and IDS/IPS
- Organizational: risk and security policies and enforcement; existing business response plans; application development, QA, and systems administration practices and capabilities
- Technical: physically confirm user privileges; application, database, network, and server configuration; and existing security technology such as firewalls and IDS/IPS
- Organizational: risk and security policies and enforcement; existing business response plans; application development, QA, and systems administration practices and capabilities
- Leverage threat intelligence to identify likely attacks
- Perform penetration and internal attacks with client team response assisted by Data Border
- Capture gaps where attacks circumvent existing technologies and controls
- Review or define metrics connecting business goals to SOC operations
- Review technical capabilities including logging and analysis to detect incidents
- Measure financial efficiency, e.g. cost per true positives and false positives
- Assess organizational relationships including MSSPs, engineering and operations collaboration, structure, funding, and people development.
- Comprehensive report and plan
- Recommended investments carefully prioritized to reflect business priorities set at project onset
- Set agile sprints prioritized to practically maximize security in incremental steps
Practicality
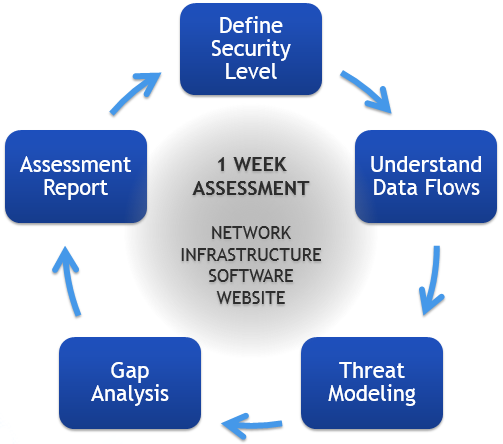
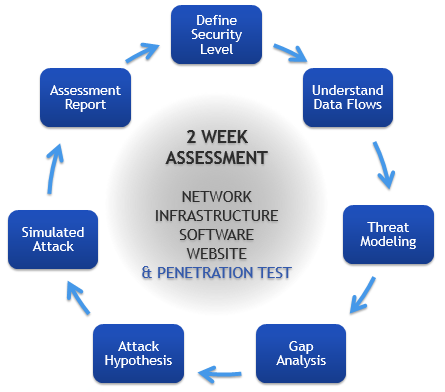
Security Assessments can start from as little a one or two weeks. Clearly the size and complexity of your organisation will determine how in-depth we can go, but in our experience rapid progress is possible.
One-Week Assessment
Two-Week Assessment
Security Assessment Report
At the conclusion of the assessment you will get a Security Assessment Report which typically includes.
- Executive summary
- Assessment scope & objectives
- Any assumptions and limitations
- Assessment tools & techniques used
- Diagrams of the environment and network as appropriate
- Security requirements
- Summary of findings and recommendations
- The general control review result
- The vulnerability test results
- Risk assessment results including identified assets, threats, vulnerabilities, impact and likelihood assessment
- Prioritised list of recommended fixes / safeguards to close issues
The Security Review methodology focuses on assessment and planning. Please see our SOC/CIRT Effectiveness service for in-depth capabilities development.
Please contact us for a free initial discussion. We can talk through your situation, how we could help build an understanding the appropriate cybersecurity defences you need and a plan to achieve them.