Loading...
Covert Channel DLP Screenshots
Installation & Processes
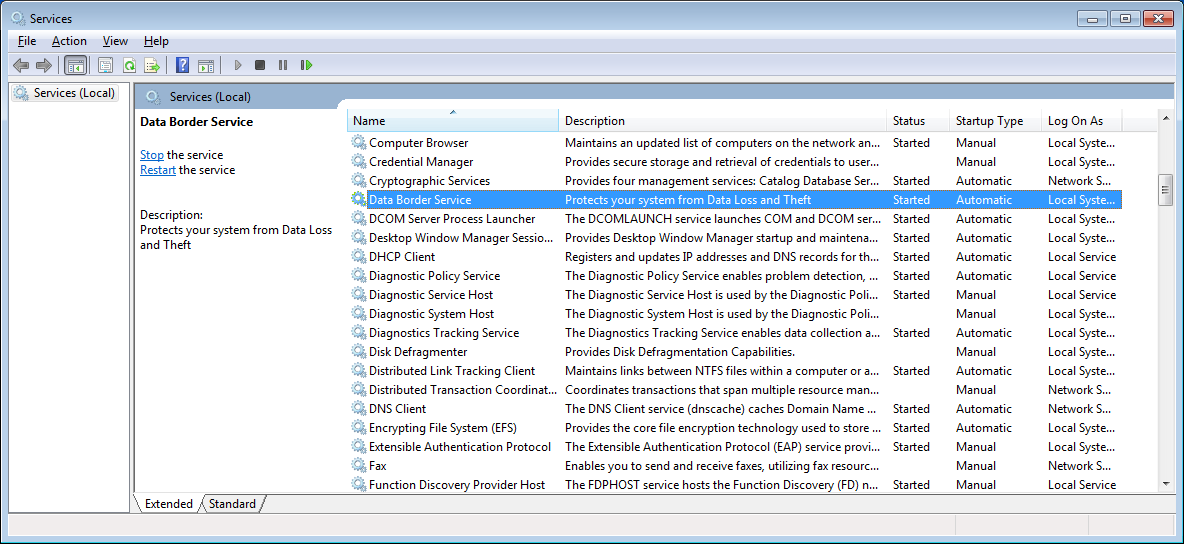
Data Border is installed on workstation PCs by an Information Security Team Administrator or an automated packaging process. It runs a service whose role is to oversee Data Border operation.
The Service starts a DataBorderDesktop process in the session of anyone who logs onto the machine. This process is the only process the user can see – ie they cannot see DataBorderDesktop processes running in other sessions or the service process. Should the desktop process be stopped, the service will automatically restart it.
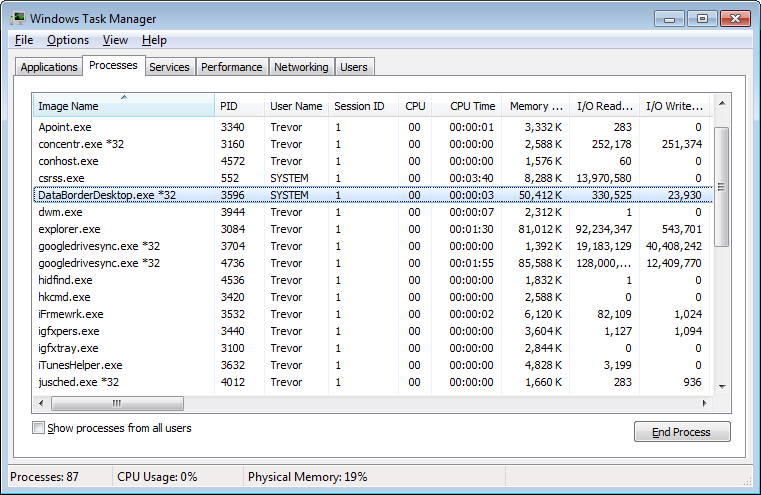
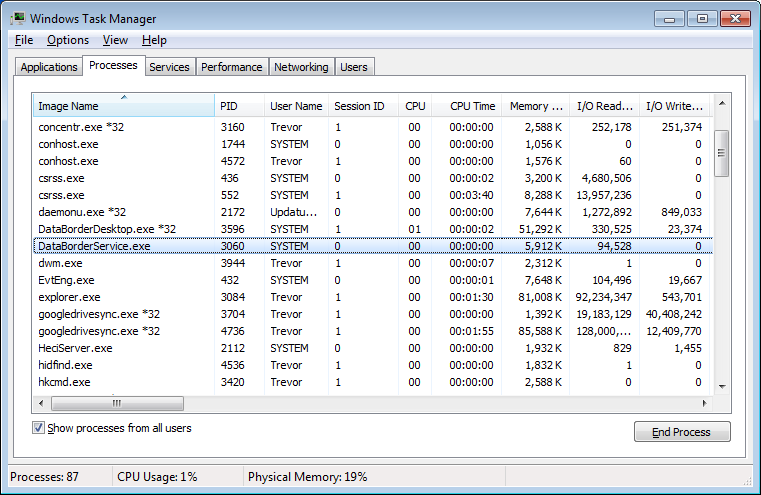
Viewing as an administrator both the Service and Desktop process can be observed. Both processes are lightweight in terms of CPU, memory usage and IO.
The Service starts a DataBorderDesktop process in the session of anyone who logs onto the machine. This process is the only process the user can see – ie they cannot see DataBorderDesktop processes running in other sessions or the service process. Should the desktop process be stopped, the service will automatically restart it.
Viewing as an administrator both the Service and Desktop process can be observed. Both processes are lightweight in terms of CPU, memory usage and IO.
The user has access to a tray icon showing them the system is operational and providing a link to the data border website which has more information.
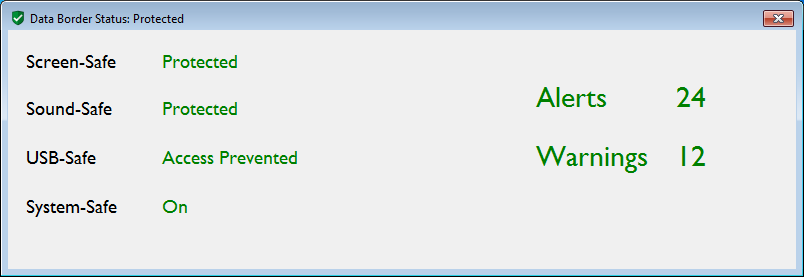
A status of the protections enabled/disabled and a summary of the alerts and warnings raised is available.
Policy Settings
Policy Settings screens provide a way for Information Security Team administrators to control the precise behaviour
of Data Border monitoring, blocking and alert escalation. These are locked down for only administrators to configure.
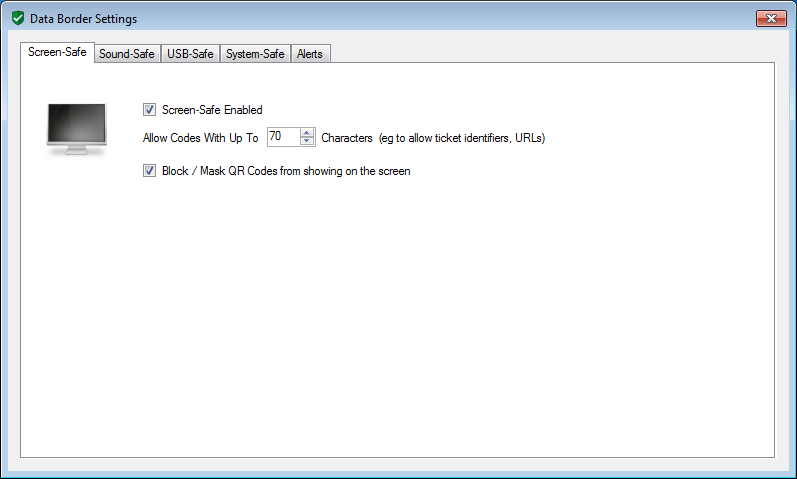
Screen-Safe Protection
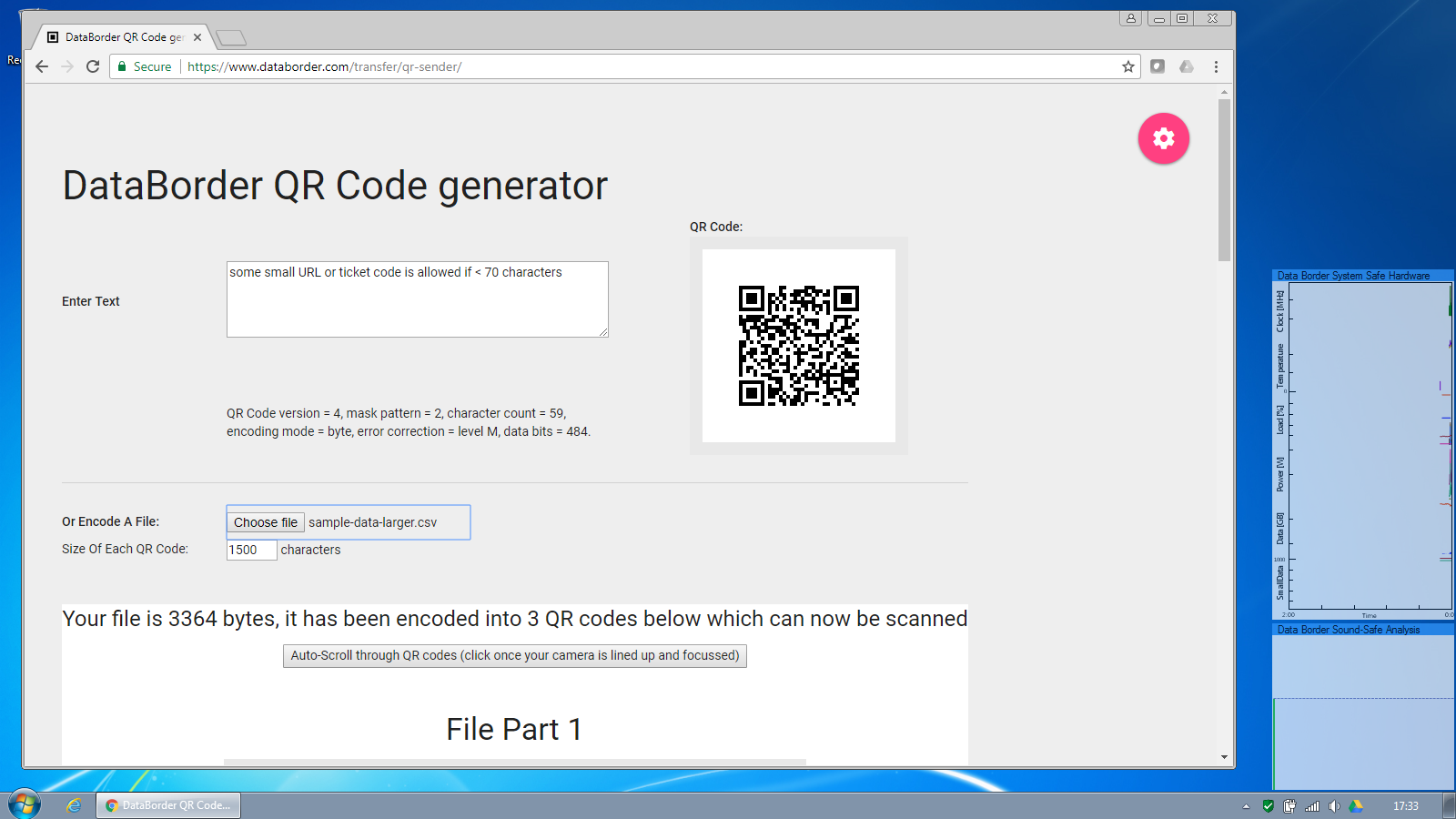
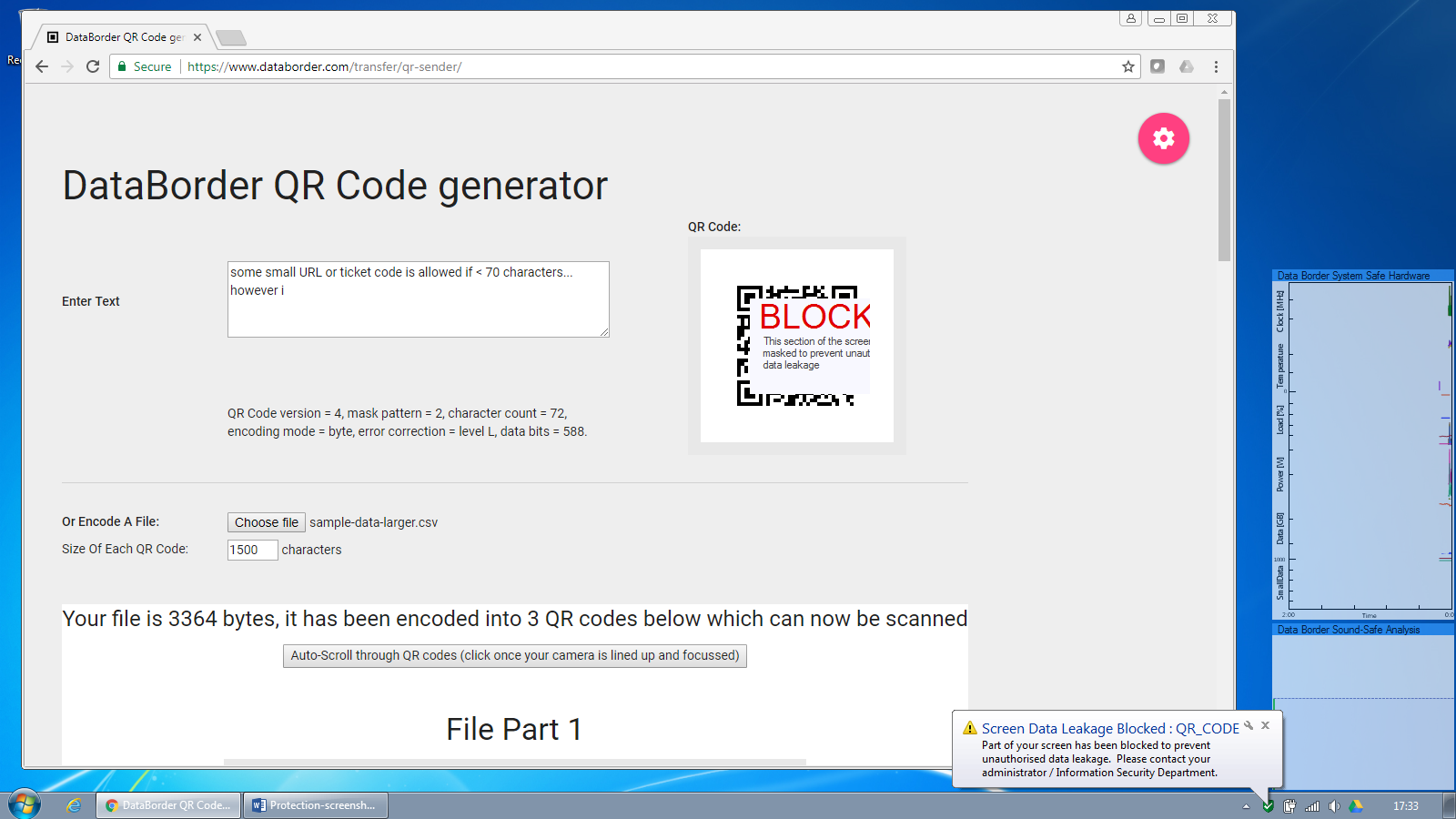
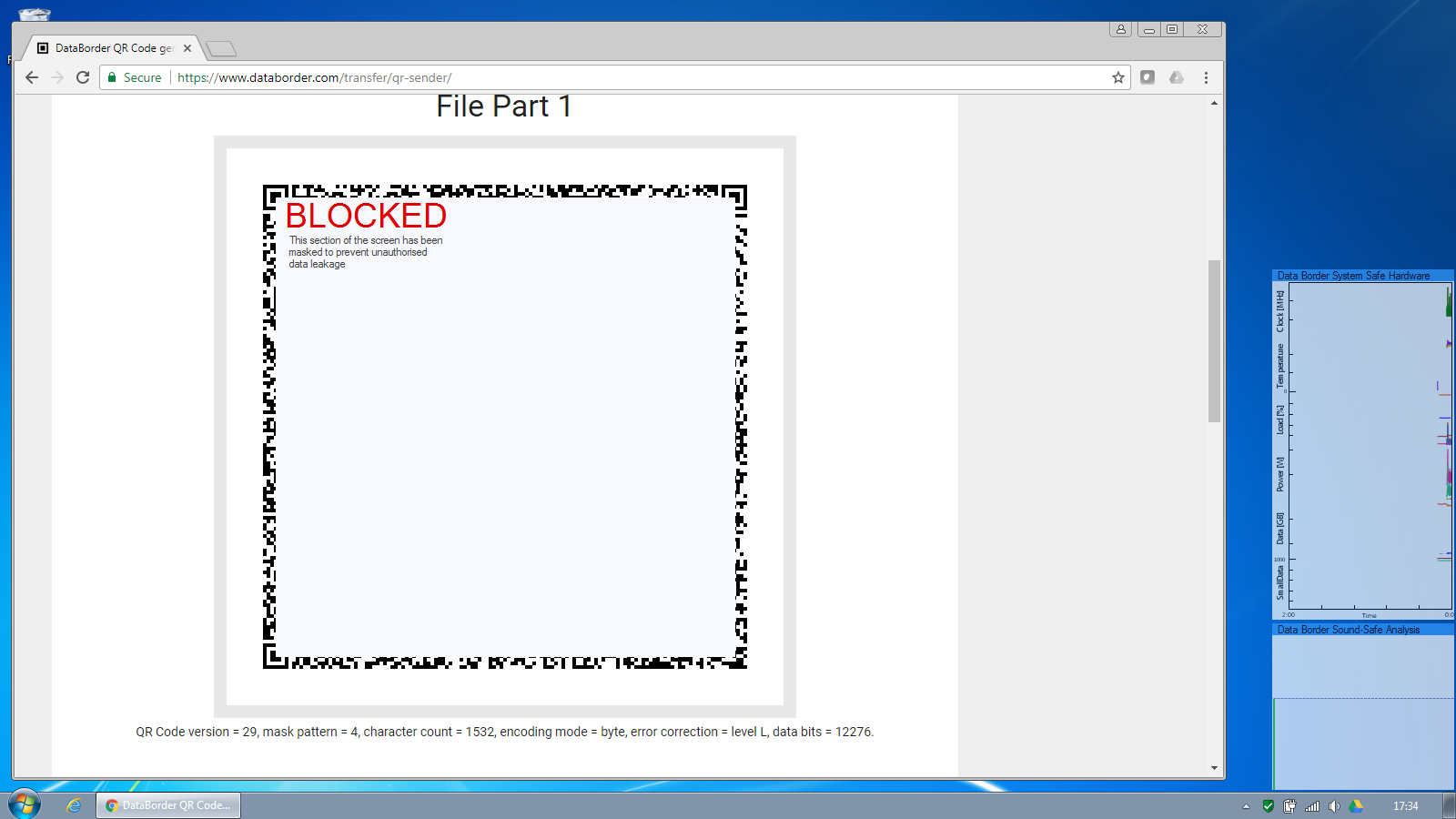
The screen safe feature allows codes containing only a small amount of data to be optionally shown untouched.
Codes larger than this threshold are blocked and an alert raised. The Information Security team is notified and optionally a warning can be displayed to the user.
Similarly attempts to output a file via the screen are blocked.
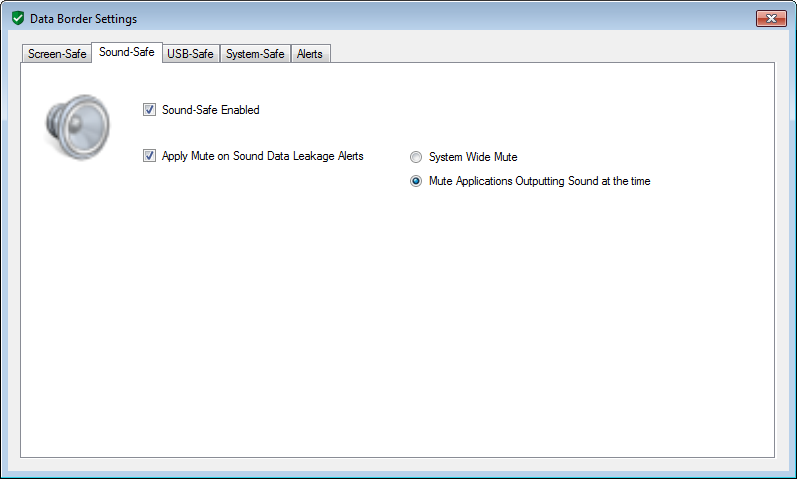
Sound-Safe Protection
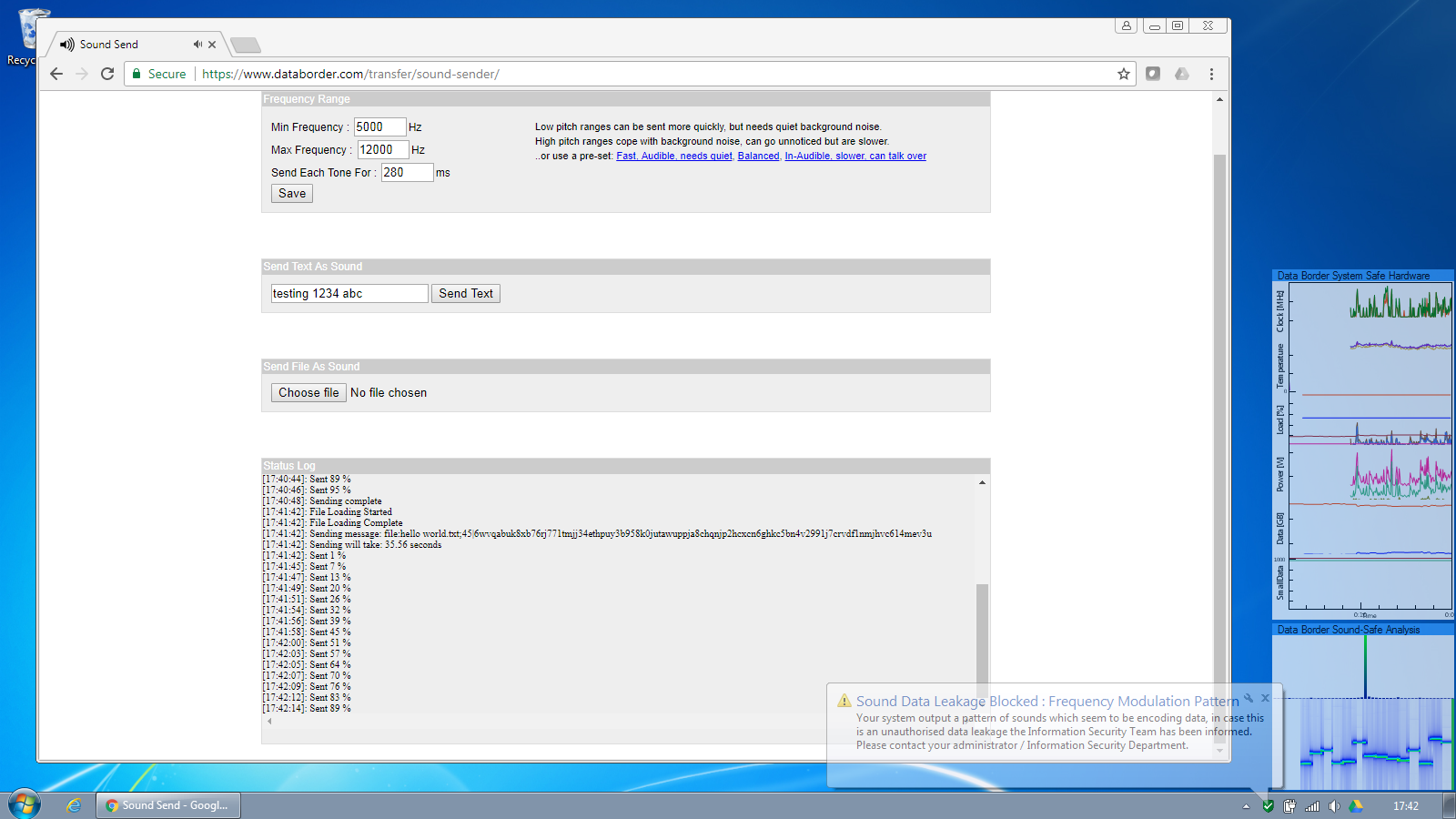
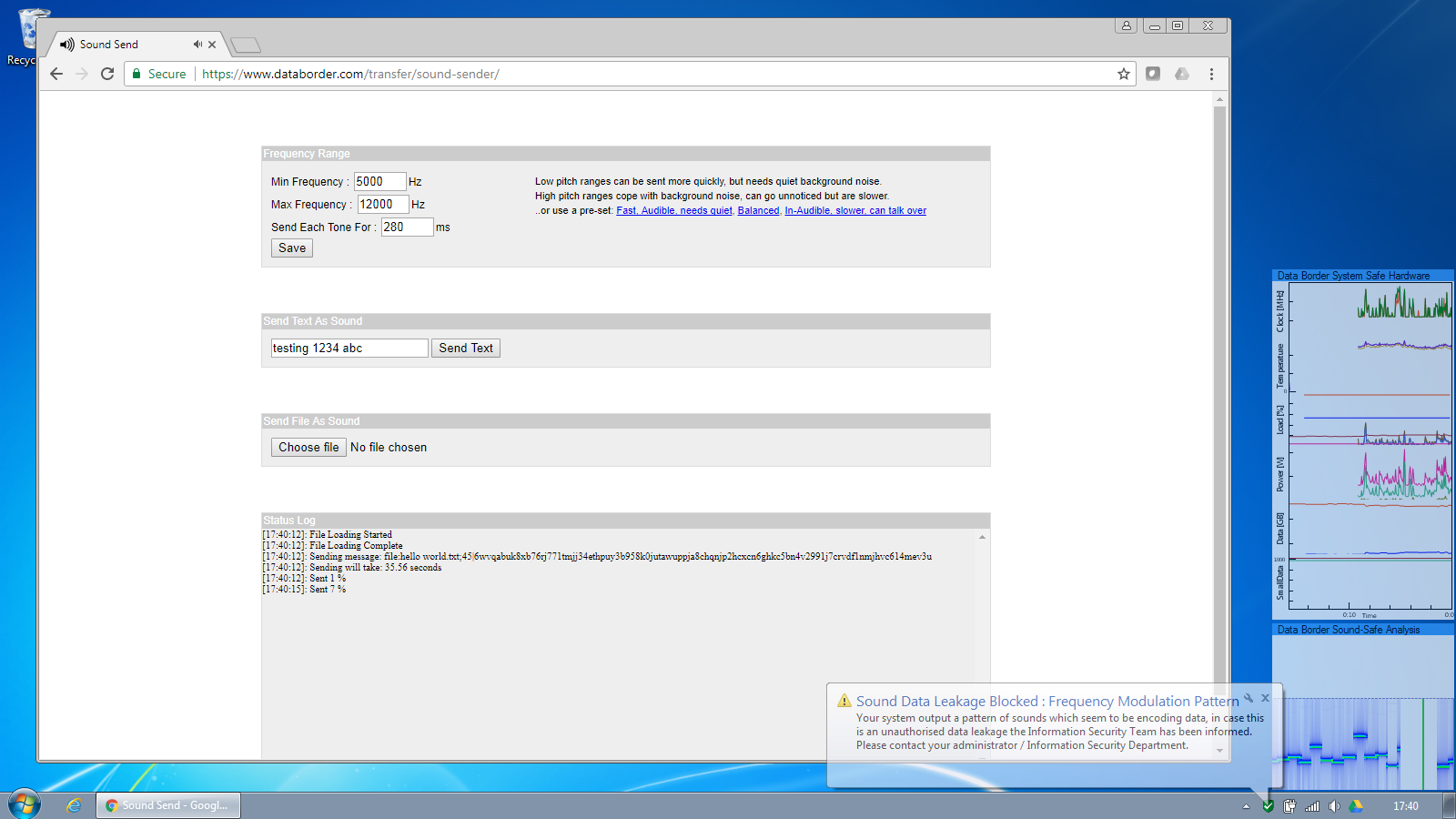
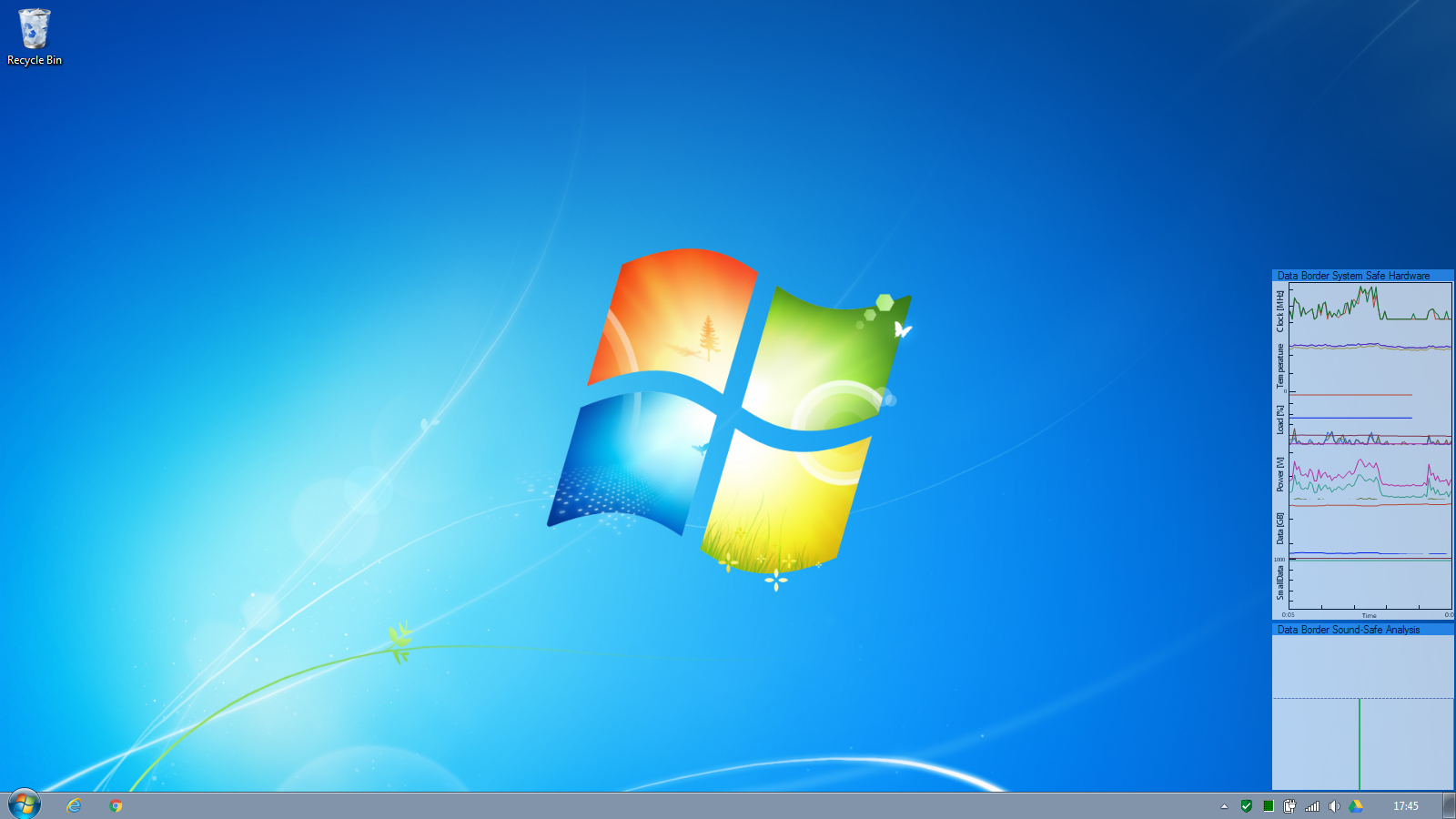
Sound safe continuously analyses the audio being output by the computer as seen in the bottom right corner of the screen.
“Normal” sound is allowed to be output as normal.
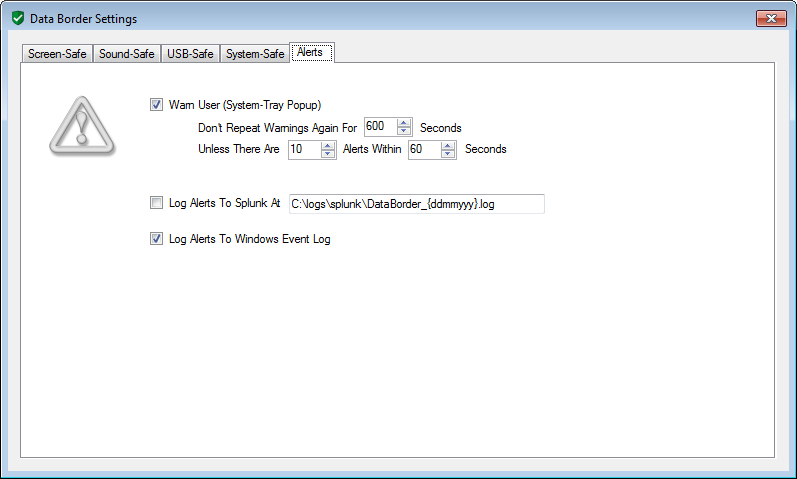
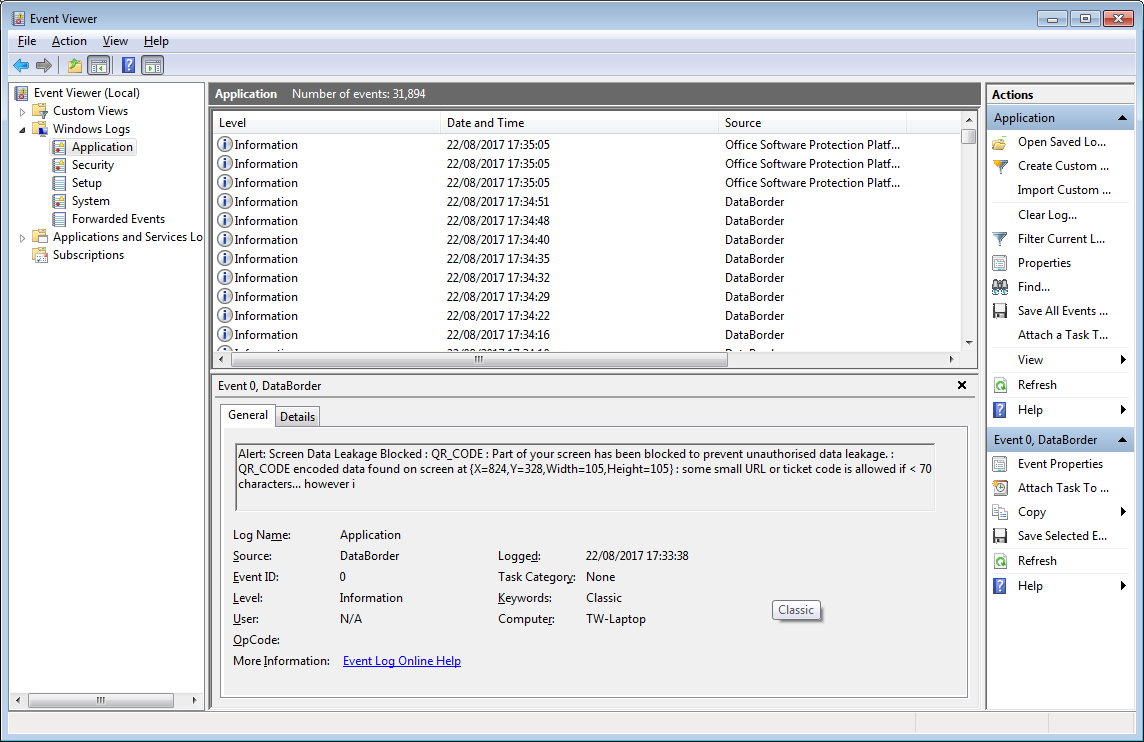
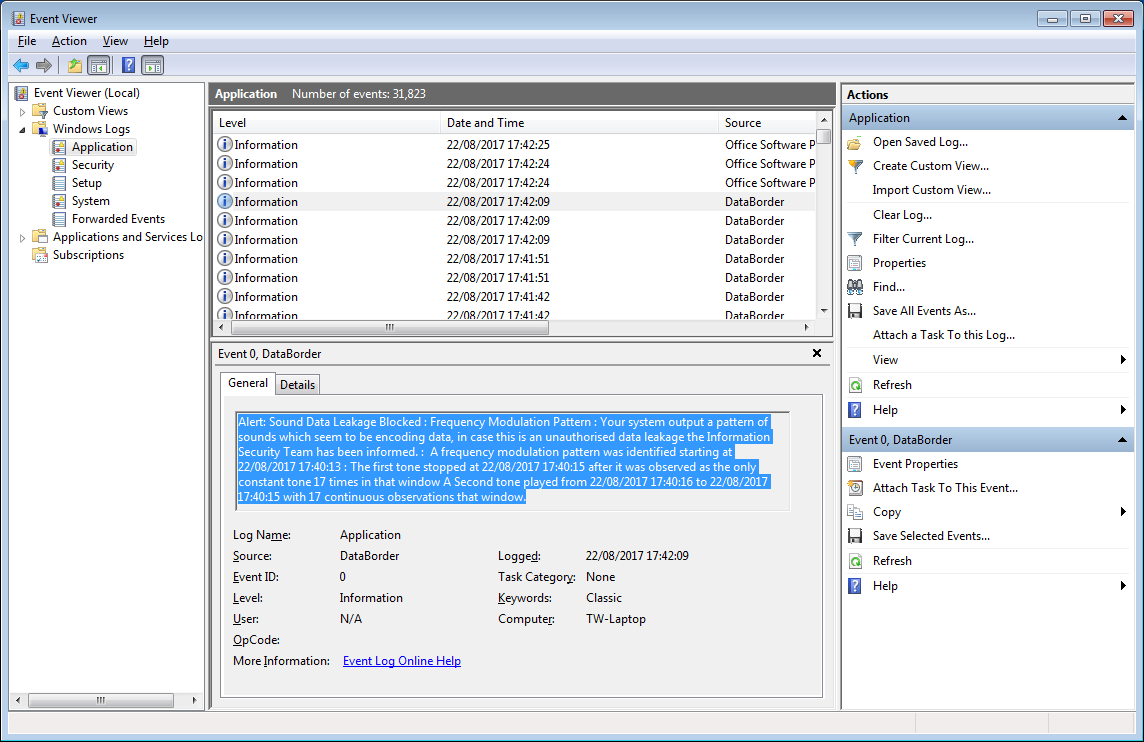
But when encoded data is attempted to be output, this is detected and blocked. An alert is raised to the information security team, according to the settings the security event is written to the windows event log, a Splunk aggregator log and/or a warning shown to the user if desired.
The user warning can be seen as the notification balloon from the windows system tray.
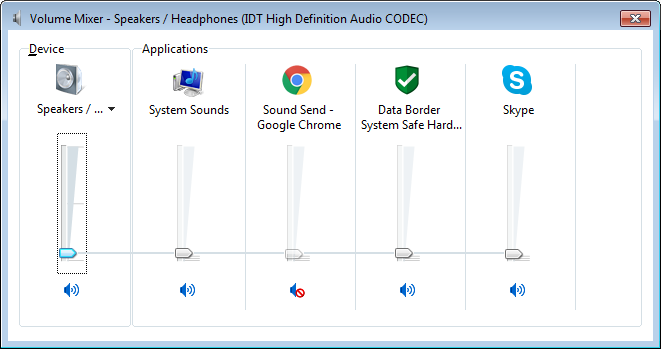
The sound output is prevented instantaneously as can be seen in the sound analysis screen. According to the Sound-Safe policy settings, either a system-wide mute of an selective mute of the application outputting the offending sound can be applied
As with the screen protection, the details of the security alert are written to the windows event log and/or written to a splunk format log file for SEIM integration.
The sound output is prevented instantaneously as can be seen in the sound analysis screen. According to the Sound-Safe policy settings, either a system-wide mute of an selective mute of the application outputting the offending sound can be applied
As with the screen protection, the details of the security alert are written to the windows event log and/or written to a splunk format log file for SEIM integration.
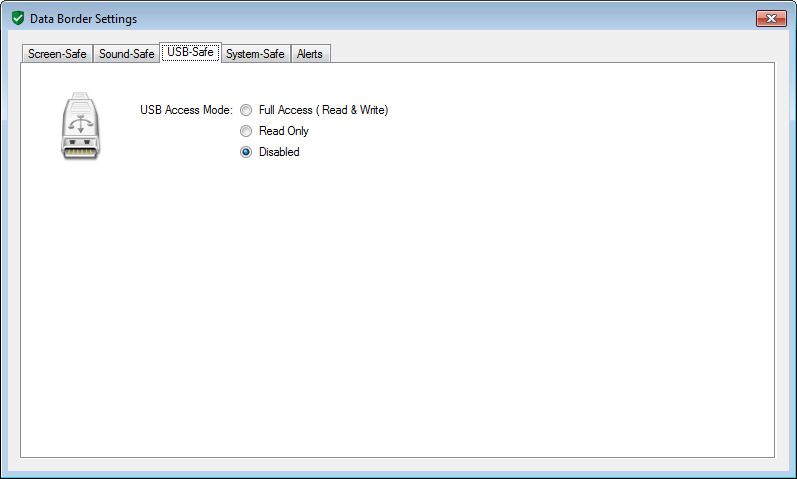
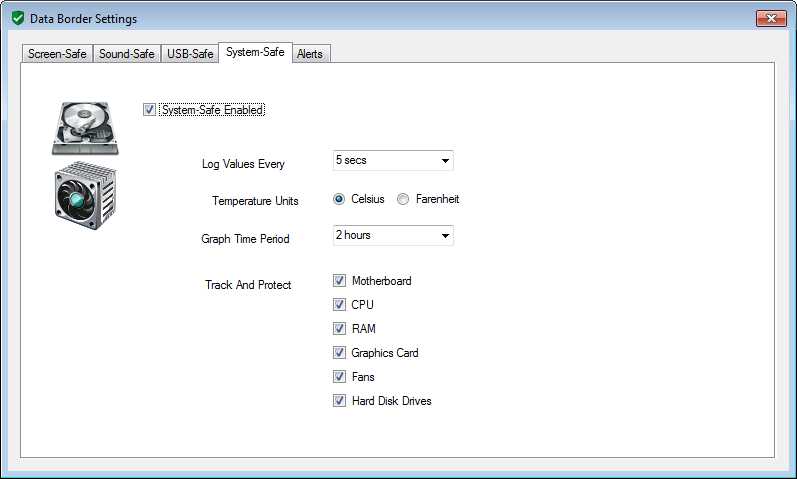
System-Safe Protection
System safe's role is to continuously analyse the
components such as temperatures, fan speed, clock speed and power levels for signs of data leakage.
If their operation deviates from normal in a way indicating that indicates modulation pattern for encoding data, a security
event is raised in the same way as screen and sound safe above.
Details of the security alert are written to the windows event log and/or written to a splunk format log file
for SEIM integration.
As computers have different hardware and sensors, System Safe adapts to monitor the installed components. In the example screenshots below we can see CPU and power usage being intentionally manipulated to give a high-low signal. The impact on temperature is subtle but just noticeable over this time-frame.
As computers have different hardware and sensors, System Safe adapts to monitor the installed components. In the example screenshots below we can see CPU and power usage being intentionally manipulated to give a high-low signal. The impact on temperature is subtle but just noticeable over this time-frame.