Loading...
Data Loss Prevention: New Vulnerable Channels
Where there's a will..
As Traditional DLP Systems have evolved to close down the
channels data leaking insiders have used, employees have found
other ways to get data out.
There are now easy ways to take digital information from organisations,
without traditional DLP detection.
Working Proof Of Concepts of
screen, sound and system component data leakage
Data Ex-Filtration Tools
How the ex-filtration works
Via on-Screen Data shown visually on the computer screen.
Just as on-screen text can be read and understood by human eyes, a smartphone or laptop camera can capture what's displayed. Encoding data (eg as QR “Quick-Read” codes) can be displayed on the screen of a corporate computer to be captured by the laptop or smartphone where it is decoded back to the original data. A data-blast sequence of QR codes can transfer data quickly.
Learn More
Just as on-screen text can be read and understood by human eyes, a smartphone or laptop camera can capture what's displayed. Encoding data (eg as QR “Quick-Read” codes) can be displayed on the screen of a corporate computer to be captured by the laptop or smartphone where it is decoded back to the original data. A data-blast sequence of QR codes can transfer data quickly.
Learn More
Via Sound output from the computer speakers, headset / headphones & line-out port.
By encoding the data as sound and outputting it from their corporate computer to another device with a microphone such as a laptop or smartphone on which the employee captures the data. This works like a one-way modem with beeps replacing the hiss of old-fashioned dial-up.
Learn More
By encoding the data as sound and outputting it from their corporate computer to another device with a microphone such as a laptop or smartphone on which the employee captures the data. This works like a one-way modem with beeps replacing the hiss of old-fashioned dial-up.
Learn More
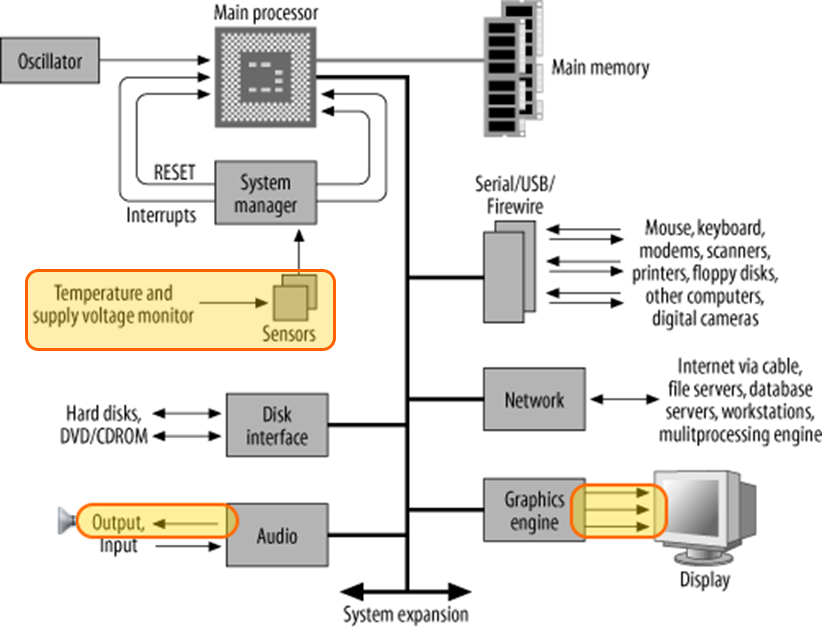
Via internal System computer components which can be manipulated to output carrying data signals.
Internal components in the computer are manipulated to make them generate a signal that can be detected outside the computer. Fans and hard-drives can create a sound signal; CPUs can be used to create a modulated temperature signature and graphics cards can be made to output data encoded in GSM frequencies to be received on a cell phone.
Learn More
Internal components in the computer are manipulated to make them generate a signal that can be detected outside the computer. Fans and hard-drives can create a sound signal; CPUs can be used to create a modulated temperature signature and graphics cards can be made to output data encoded in GSM frequencies to be received on a cell phone.
Learn More
Via The Computer Screen
There are few computers without a screen - employees need to see the screen to work. The intention is that information shown on the screen is just for users to interactively work with, but there's nothing to stop data being displayed in a way that a can be read by another device with a camera and decoded back into data.
With DataBorder
The DataBorder Screen-Safe feature monitors the computers screen(s) for QR codes and other methods of visually encoding data. It can optionally allow codes containing only a small amount of data to be shown untouched.
QR codes above this threshold are blocked and an alert raised. The Information Security team is notified and optionally a warning can be displayed to the user.
The DataBorder Screen-Safe feature monitors the computers screen(s) for QR codes and other methods of visually encoding data. It can optionally allow codes containing only a small amount of data to be shown untouched.
QR codes above this threshold are blocked and an alert raised. The Information Security team is notified and optionally a warning can be displayed to the user.
Encode Data As Sound And Play It Through Computer Speakers / Headphones
Just as dial-up modems used to do before broadband internet connections, data can be encoded as sound and transmitted to a listener to reconstruct back into data at the other end. Office computers are increasingly used as IP phones, for conference calls & training so have speakers and headphones. There's nothing to stop the output being data carrying beeps rather than a conversation.
Unprotected
Like the screen example, a simple web-page gives all that's needed to read in any file the user has access to, encode it into a series of tones and play them through the computers speakers, headphones or aux port. All that's needed to pick these up is a smartphone, a laptop with a microphone or a sound recorder to save the audio for decoding later. By using frequencies outside the human hearing range, this can even be done in an office full of people with nobody noticing.
Like the screen example, a simple web-page gives all that's needed to read in any file the user has access to, encode it into a series of tones and play them through the computers speakers, headphones or aux port. All that's needed to pick these up is a smartphone, a laptop with a microphone or a sound recorder to save the audio for decoding later. By using frequencies outside the human hearing range, this can even be done in an office full of people with nobody noticing.
With DataBorder
With DataBorder Sound-Safe the audio the computer outputs is constantly monitored and analysed for patterns indicating data transfer. Machine learning, frequency & beat analysis detect data encoded as sound but let normal sound like conference calls or training videos play as normal. If encoded data is attempted to be output, this is detected and blocked by muting the program that output it; an alert is raised to the information security team.
With DataBorder Sound-Safe the audio the computer outputs is constantly monitored and analysed for patterns indicating data transfer. Machine learning, frequency & beat analysis detect data encoded as sound but let normal sound like conference calls or training videos play as normal. If encoded data is attempted to be output, this is detected and blocked by muting the program that output it; an alert is raised to the information security team.
By Manipulating Components Within The Computer To Produce A Signal
Some computer systems are so sensitive that they are intentionally separated from the rest of the world. Systems like Government networks with secret data, power-station or manufacturing controls are "Air-Gapped" in an attempt to isolate them from infection, hacking and data leakage. Researchers have demonstrated ingenious ways to get data out of air-gapped systems, without a network connection, removable drives and even without outputs like screens or speakers used above. Internal components can be manipulated to produce a signal capable of carrying data and a nearby sensor collects and interprets the signal on the unorthodox data channel.
Unprotected
Here the computer is manipulated in a way that it's internals emit a signal for a waiting receiver to collect.
Here the computer is manipulated in a way that it's internals emit a signal for a waiting receiver to collect.
- "Fansmitter" changes the computer fan speed to produce vibrations/sound for a listening microphone.
- Vibrations caused by accessing the hard-drive in patterns can also be listened for.
- The CPU can be heavily worked to modulate the temperature for a [potentially long-distance] thermometer to pick up.
- A light sensor or camera can receive data encoded by flashing LEDs such as caps-lock on a keyboard & network status lights.
- Processors can be used to generate GSM frequency radio waves for a nearby mobile phone to receive.
With DataBorder
DataBorder System-Safe uses statistical and machine learning analysis to search for abnormal patterns in the usage of each sub-component in machines it protects. The sensors like temperature and usage patterns are continuously modelled and if/when a data carrying signal is detected an alert can be raised.
DataBorder System-Safe uses statistical and machine learning analysis to search for abnormal patterns in the usage of each sub-component in machines it protects. The sensors like temperature and usage patterns are continuously modelled and if/when a data carrying signal is detected an alert can be raised.
.png)
.png)
.png)
.png)
.png)
.png)